|
DAWN Security
XXXXXXXXX
XXXXXXXXX
Phone: 555 111 2222
Fax: 555 111 2233
E-Mail: enquiries@dawnsec.com
URL: http://www.dawnsec.com
Network Security Penetration Test Conducted on behalf of Little Company Network Inc. Authors: Daniel Newman, Andrew Whitaker Version: 1.0 Date: 05/05/05 Company Name: | LCN, Little Company Network | Title: | Penetration Test (Black Box) | Date: | May, 2005 | Document Classification: | Confidential |
Executive Summary Objective The test was commissioned and conducted to determine potential vulnerabilities at the perimeter of the LCN network infrastructure. Methodology The test was conducted as a black-box test with only the following information made available: With no prior knowledge of the company or its network infrastructure, the testing strategy was to take the approach of a malicious attacker. Probing the attack surface was to take place, and this was broken down into the following elements: Website Wireless networking
Findings The nature of the test dictated that we would obtain as much information as possible in 24 hours. Our findings reflect this. Summary Test | Result | Severity Level |
|---|
Trace Route | Website location is in Corvallis Oregon. | Low | Wireless Access | WEP authentication in use and noncommercial standard hardware in use. | High | Port Scan | Only Port 80 is open on the external; all internal ports are open. | Low/High | Firewall Security | External is fine; however, the internal has Telnet enabled, allowing easy access to the device. | Low/High | Service Pack Management | Servers were service-packed to current or near-current level. | Medium | Web Server Security | Server not inherently insecure, but hosted application poses significant risk. | Critical | Network Privileges | Unknown computers can connect to the network. | High | Database Security | Inappropriate use of sa account and vulnerable to SQL injection attacks. SQL Server service is being executed by the Local System Account. | Critical | FTP Server Security | No vulnerable FTP access discovered. | Unknown | Mail Server Security | Insufficient time available to test mail services. No mail server was found. | Unknown |
Graphical Summary Figure 16-8 summarizes the vulnerabilities as detailed above. The severity levels can be interpreted as follows: Figure 16-8. Risk Severity Level 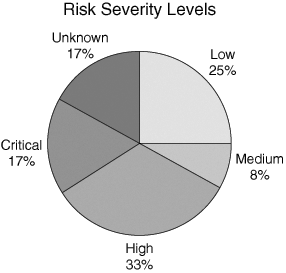
Level | Description |
|---|
Low | Little risk of exploitation. No recommendation to take immediate remedial action. | Medium | Limited risk in isolation, but might have an impact in combination with other discovered vulnerabilities. Recommendations should be noted and scheduled for implementation. | High | Known vulnerability with a high probability of exploitation. Recommendations should be acted upon immediately. | Critical | Known vulnerability with cursory exploitation. Remedial work should be immediate. |
Technical Testing Report Black-Box Testing Trace Route Security |
|---|
Severity | Low. | Summary | Tracert and TraceRoute command displayed the location of the web server. | Recommendations | Disable ICMP traffic on the firewall. |
Wireless Network |
|---|
Severity | High. | Summary | WEP was able to be cracked in a matter of hours using standard equipment. | Recommendations | Remove all current wireless access points. Replace access points with devices that contain better security than WEP, such as WPA. |
Port Scan |
|---|
Severity | Low/High. | Summary | External port scans revealed good security on the firewall. Only port 80 was open for attack. However, internal network port scans revealed the entire network and identified internal operating systems. | Recommendations | Disable all unused services and applications on computers. Enable IPSec for internal network traffic. |
Firewall |
|---|
Severity | Low/High. | Summary | No external access for the firewall was detected; however, the internal side of the firewall has Telnet enabled on it, allowing a potential access point to inside the firewall. | Recommendations | Disable Telnet on the firewall. Use SSH if remote configuration is required. Disable ICMP on both sides of the firewall. Link firewall username and passwords with TACACS+ or RADIUS servers. |
Service Pack Management |
|---|
Severity | Medium. | Summary | Several computers are service packed to a fairly current level. | Recommendations | Stay up-to-date on all hot fixes and service packs. Implement a policy for updating. Implement automatic updating. |
Web Server |
|---|
Severity | Critical. | Summary | Web server itself is fairly secure; however, the application (website) is not secure. SQL injection attacks allowed complete access to the internal network. | Recommendations | Have website developers rework the website and prevent SQL injection attacks. |
Network Privileges |
|---|
Severity | High. | Summary | Any unknown computer is allowed access to the network. | Recommendations | Port security on switches can help to increase security by only allowing known MAC address on the network. |
Database Security |
|---|
Severity | Critical. | Summary | The website was found to be vulnerable to SQL injection attacks, allowing a malicious attacker to query the internal database for all of its information. As a result, the attacker can steal the entire contents of the database. The connection string used to access the database from the web application granted an unnecessary level of privilege at the database level. It was discovered to be using the sa (System Administrator) login. As a result of the above, an attacker would have the means and privileges to execute any valid SQL command against the database server. | Recommendations | Implement tighter input validation. Replace any direct SQL statements with stored procedures. Configure the web application to connect to the database under an account with only the privileges it requires to function. Change the service account used by SQL Server from the local system account to a standard user. |
FTP Server |
|---|
Severity | Unknown. | Summary | No FTP servers were found in the time frame given. | Recommendations | None. |
Mail Server |
|---|
Severity | Unknown. | Summary | No mail servers were found, and time did not permit access to find them. | Recommendations | Perform penetration test that targets this area. |
This section of the report could contain all of the network maps and enumerations carried out for each of the computers within the LCN networks for verboseness. Presenting and Planning the Follow-Up The final step of the report consists of presenting the report to the company and discussing the findings. Typically, the customer wants you to give total iron-clad fixes for him; however, the liability of saying something like, "Oh, yes. SP 2 will totally protect you" is avoided at all possible costs. Leaving the fixes to the customer is the best practice. The meeting tends to be around a table, with the systems administrators reviewing items in the report line by line. It might be beneficial to demonstrate vulnerabilities of the customer system. After the customer is satisfied, the only copy of the report is handed over, and all notes and scripts used to penetrate the LCN network are destroyed. The last point to make to LCN is to determine when it would like to do the follow-up. Even if LCN implements all the changes to help secure its network, the penetration team needs to test these fixes again and again. Every day, new methods and techniques are discovered. Regularly scheduling a penetration test helps to minimize company risk. |
