| The J2EE platform is essentially a Java-based distributed computing environment that defines the multi-tier application architecture best suited for building enterprise applications. The multi-tiered architecture is based on the notion of logical partitioning of self-contained components. The logical partitioning encapsulates related functional components of unique responsibility and delivers their functionalities through well-defined interfaces (see Figure 5-1 J2EE Platform and its logical tiers). Figure 5-1. J2EE Platform and its logical tiers 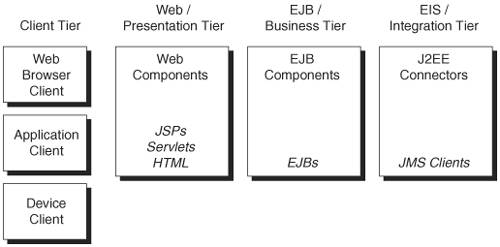
The J2EE platform is generally represented with the following logical tiers shown in Figure 5-1: Client Tier: The client tier represents the J2EE platform's user interface or its application clients that interact with the J2EE platform-based application or system. A typical client can be a Java application (J2SE/J2ME), Java applet, Web browser, Web service, Java enabled device, or Java-based network application. Web or Presentation Tier: The presentation tier represents the presentation logic components required to access the J2EE application and its business services. It handles the requests and responses, session management, device-independent content delivery, and invocation of business components. From a security standpoint, it delivers client login sessions and establishes single sign-on access control to underlying application components. J2EE components such as JSPs, Servlets, and Java Server Faces (JSF) reside in the Web container, which delivers user interfaces to clients. In J2EE 1.4, Web services-based communication can also be delivered using Web components such as Servlets. Business or Application Tier: The Business Tier represents the core business logic processing required. It typically deals with business functions, and transactions with back-end resources, or workflow automation. In some cases, it acts as a business wrapper when the underlying resources handle the actual business logic. EJB components such as Session Beans, Entity Beans, and Message-driven Beans reside in this tier. In J2EE 1.4, Stateless EJB components can be exposed as Web services and can be invoked using SOAP-based Web services communication. Integration or EIS Tier: The Integration Tier represents the connection and communication with back-end resources such as Enterprise-information systems (EISs), database applications, and legacy or mainframe applications. The business-tier components are tightly coupled with the Integration Tier in order to facilitate data query and retrieval from back-end resources. J2EE components such as JMS, J2EE connectors, and JDBC components reside in this tier. Resources Tier: The resources tier represents the back-end application resources that contain data and services. These resources can be database applications, EIS systems, mainframe applications, and other network-based services.
The components in these tiers are executed inside of component-specific containers such as a Web container or an EJB container. Containers provide the environment in which the components can be executed in a controlled and managed way. They also provide an abstraction layer through which the components see the underlying services and the architecture. The J2EE platform provides a full-fledged security infrastructure and container-based security services that address the end-to-end security requirements of the different application tiers and their resources. To define security at all levels, the J2EE platform defines contracts that establish the security roles and responsibilities involved in the development, deployment, and management of a J2EE application. In accordance with J2EE specifications, the security roles and responsibilities involve the following: J2EE Platform Provider: The J2EE server vendor who is responsible for implementing the J2EE security infrastructure and mechanisms. J2EE Application Developer: The application developer who is responsible for specifying the application roles and role-based access restrictions to the components. J2EE Application Assembler: The component builder who is responsible for assembling the components and defining the security view identifying the security dependencies in the component. J2EE Application Deployer: The component deployer who is responsible for assigning the users and groups to the roles and who establishes the security deployment scenarios.
The above roles and responsibilities ensure security at every stage of development and deployment of all components and their residing application tiers. Before we delve into the J2EE security mechanisms, let's take a look at the J2EE security definitions, which are used to describe the security of a J2EE environment. |
